As part of Google’s component of its initiative aimed at the deployment of quantum-resistant cryptography, Google is pleased to declare the launch of the primary quantum-adaptive FIDO2 security key implementation. This implementation is now integrated into OpenSK, their open-source security key firmware. The hardware-centric open-source design of this implementation has been strategically crafted, incorporating an innovative ECC/Dilithium hybrid signature framework. This framework harnesses the robust security attributes of ECC in the face of standard attacks, while also leveraging the quantum-resilient qualities of Dilithium against quantum-based attacks. This collaborative schema was jointly developed in partnership with ETH Zürich, and it earned the distinction of the best paper at the ACNS Secure Cryptographic Implementation Workshop.
As advancements toward practical quantum computers gain momentum, the imperative to prepare for their impending arrival heightens over time. Specifically, the challenge lies in addressing the emergence of quantum computers as a pressing concern. Conventional public key cryptography initially devised to safeguard against classical computers, is poised to falter in the face of quantum attacks. A positive development in this context is the recent standardization of public key quantum resilient cryptography, which encompasses the Dilithium algorithm. This development charts a clear pathway to ensuring the security of security keys against potential quantum attacks.
While quantum attacks remain a prospect for the distant future, the extensive deployment of cryptography across the expanse of the Internet represents a formidable undertaking. This underscores the significance of initiating this endeavor at the earliest juncture. Notably, the process of securing security keys is expected to unfold gradually for users. The acquisition of new security keys will become a necessity once FIDO undertakes the standardization of post-quantum cryptography resilient cryptography. The ultimate adoption of this new standard hinges on receiving support from major browser vendors.
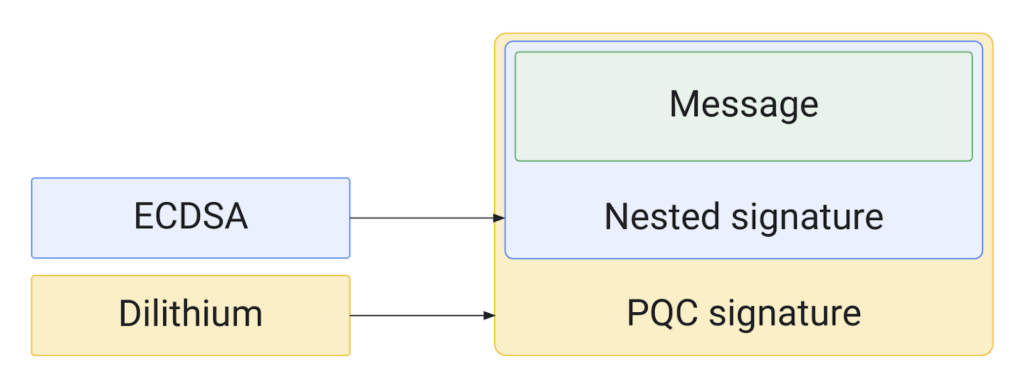
The proposed implementation utilizes a hybrid strategy that combines the well-established ECDSA signature algorithm with the recently standardized quantum-resistant signature algorithm known as Dilithium. This innovative hybrid signature schema, developed in collaboration with ETH, presents a blend of advantages from both algorithms. Employing such a hybrid signature system is crucial due to the fact that the security of emerging quantum-resistant algorithms, including Dilithium, has not yet been established over time. Recent attacks on Rainbow, another quantum-resilient algorithm, highlight the necessity for caution. This cautious approach is especially warranted for security keys, considering that the majority cannot be updated – although efforts are underway to achieve this for OpenSK. Notably, the hybrid approach finds application in other post-quantum initiatives, such as Chrome’s implementation of TLS support.
From a technical standpoint, a significant hurdle involved crafting a compact Dilithium implementation capable of functioning on the limited hardware of security keys. By meticulously optimizing the code, a memory-efficient Rust implementation of Dilithium was devised, consuming a mere 20 KB of memory, which proved sufficiently compact. Efforts were also invested in ensuring that the implementation’s signature speed aligned with the stipulated security key specifications. However, the team holds the belief that enhancing signature speed through the utilization of hardware acceleration could enhance key responsiveness.
As the initiative progresses, there’s a hopeful aspiration for the integration of this implementation, or a modified version thereof, into the FIDO2 key specification. The ultimate goal is for major web browsers to support it, thereby safeguarding user credentials against quantum attacks. For those interested in testing this algorithm or contributing to the realm of security key research, engagement with the open-source implementation, OpenSK, is encouraged.