In my previous post on Cybersecurity on Small and Medium Sized Businesses it was established that SMBs are not immune to cyber-attacks. Cyber-attacks are on the rise, and a vast majority of criminals have turned their focus on SBMs because they have determined that it brings less attention and understand that most of these businesses do not have a plan of action in place or the resources and infrastructure to detect and prevent these attacks. In truth, these criminals do not discriminate based on your location, industry, or size. In order for us to further understand these attacks we must establish a basis of why someone would engage in cyber-attacks.
IBM (n.d) makes a pretty good summary of why these attacks are carried out, and they range from “petty theft to acts of war.”
- Financial Gain
- Financial Data
- Client list and data (Social Security, addresses, etc)
- Login Credentials
- Intellectual Property, trade secrets.
- Showing off skillsets
Others are driven by social, political, or religious beliefs. Yet sometimes these are deliberately caused from the inside by your everyday office worker but can range to nation-state cyber-attacks. Nevertheless, on a basis, there is a deliberate effort to steal, expose, alter, disable, or destroy data, applications, and other assets through unauthorized access (IBM, n.d)
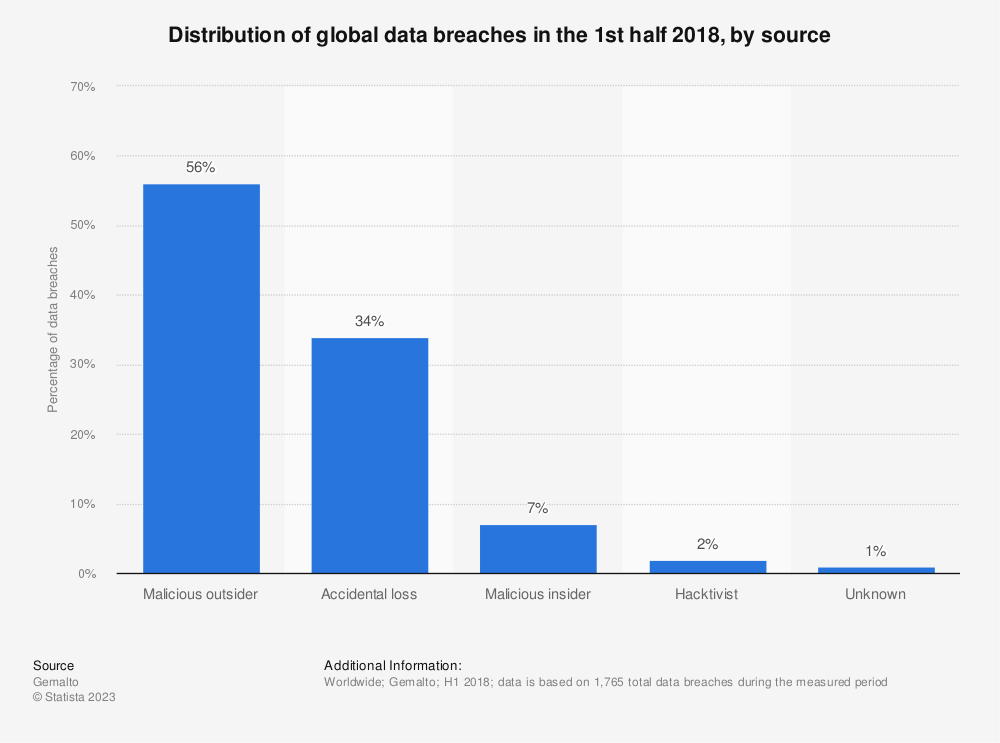
Most of these external parties are considered by professionals as “malicious outsiders.” These malicious outsiders can be classified into categories, and it is they that SMBs should focus on as they prey on small businesses.
- Hackers – According to CISCO, a hacker is a person who breaks into a computer system. These individuals can do it for financial gain, while some do it simply for fun. Those with malicious intent typically further install malicious software, steal, delete, or modify data, and others disrupt system services. They usually have a bag of tricks that are ready to exploit the many vulnerabilities in a system.
- Hacktivists – While hacking means breaking into computer systems, activism promotes social perspectives. As a result, hacktivism is a combination of the two (Fortinet, 2022). These are the individuals who are driven and will target your business for social, political, or religious beliefs. SMBs are involved in different sectors, and it is without prejudice that one can be targeted.
- State-Sponsored-Warfare – While the chances of an SMB being a direct target of a state-sponsored attack are minimal, the possibility still exists. One can be an independent contractor for the government, or deal with sensitive and confidential intellectual property data. These highly sophisticated attacks are launched on a larger scale and would be difficult for an SMB to mitigate. InfoSecurity Magazine (2023) showcases a specific example where SMBs were targeted in phishing attacks by state-aligned threat actors from Russia, Iran, and North Korea in 2022-2023.
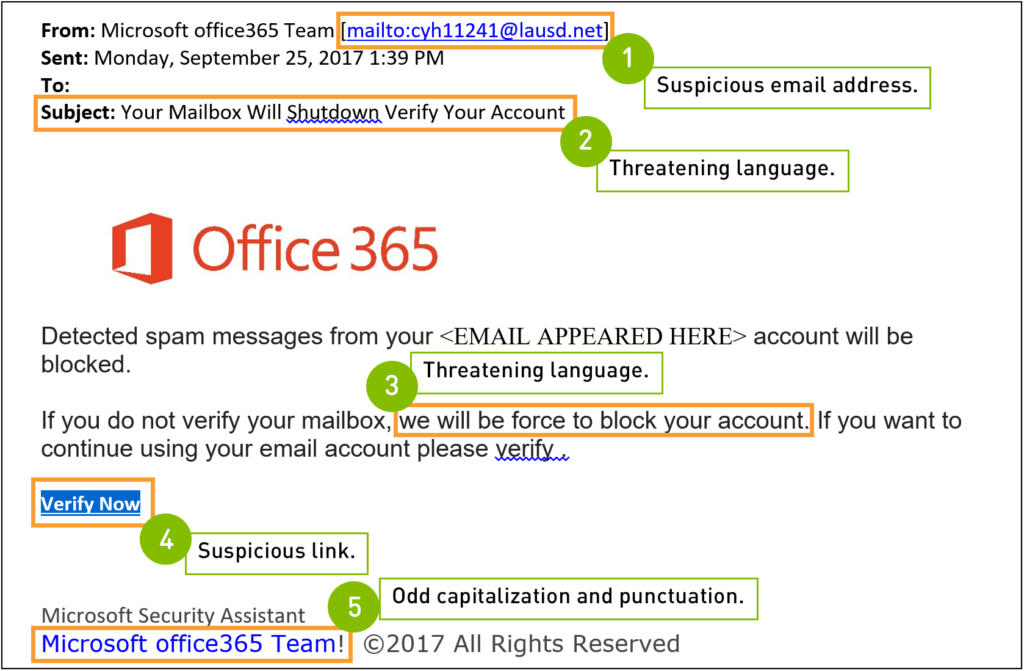
- Phishers – These criminals contact victims via email, telephone, or text messages posing as a legitimate institution to “fish/phish”, and lure individuals into providing sensitive data such as passwords, credit card information, and IDs. When they obtain the data it can lead to identity theft or financial losses. These phishing emails or messages always have a sense of (urgency, questionable hyperlinks, attachments for downloads, unusual senders, and eye-catching lucrative offers). According to IBM, this is one of the most common threats and the most common kind of cyberattack. These can even deliver malware to your systems that open up further backdoors that can exploit systems (IBM, n.d).
Nevertheless, not all cyberattacks come from the outside. There are also malicious insiders. The Cybersecurity and Infrastructure Security Agency (CISA) point out that a malicious insider is one that uses their authorized access or understanding of an organization to harm that organization. It can include “malicious, complacent, or unintentional acts that negatively affect the integrity, confidentiality, and availability of the organization, its data, personnel, or facilities.” This of course can come from something as simple as a disgruntled employee to one engaging in espionage. Securonix (n.d) shares a really good story of Edward Snowden who was an IT contractor, employed by Booz Allen to provide services to the US Intelligence who later leaked out perhaps the greatest amount of US state secrets.
References:
CISCO. (n.d). What is a Hacker? Retrieved from https://www.cisco.com/c/en/us/products/security/what-is-a-hacker.html
Fortinent. (2022). Hacktivism – A Cyberattack? Meaning, Types, and More. Retrieved from https://www.fortinet.com/resources/cyberglossary/what-is-hacktivism
IBM. (n.d) What is a Cyberattack? Retrieved from https://www.ibm.com/topics/cyber-attack#:~:text=Outsider%20threats%20aren’t%20authorized,%2C%20amateur%20hackers%2C%20and%20hacktivists.
IBM. (n.d). What is Phishing? Retrieved from https://www.ibm.com/topics/phishing
InfoSecurity Magazine. (2023). SMBs Targeted by State-Aligned Actors for Financial Theft and Supply Chain Attacks. Retrieved from https://www.infosecurity-magazine.com/news/smb-targeted-apt-financial-supply/
Infrastructure Security Agency. (n.d). Defining Insider Threats. Retrieved from https://www.cisa.gov/topics/physical-security/insider-threat-mitigation/defining-insider-threats
Securonix. (n.d). Edward Snowden – The Ultimate Insider Threat. Retrieved from https://www.securonix.com/blog/edward-snowden-the-ultimate-insider-threat/

