On March 29th, 2023 Reddit User IanBerk-HawkinsMSP posted that he’d recently taken a day off only to come back and be greeted with a ransomware infection. All of the files had been encrypted with a .Akira file extension. Ransomware is a serious cybersecurity concern, and it is one of the most effective methods of cybercrime that have wreaked havoc in recent times. For those unaware of ransomware, it is a form of malicious software that encrypts/locks your computers and/or files and in return demand a ransom for its release (Kaspersky, n.d). This in return typically results in severe consequences ranging from financial and data loss, damage to reputation, and downtime of critical systems.
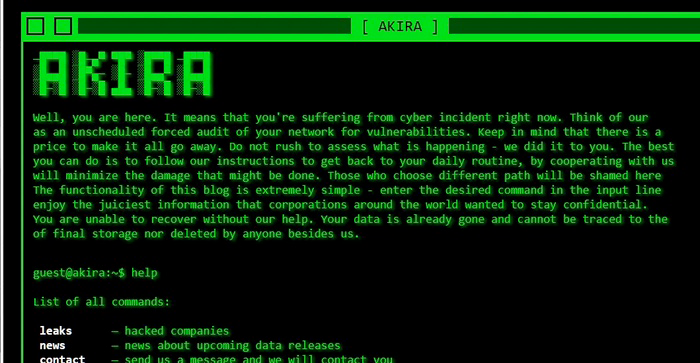
As of June 29th, 2023, the Akira ransomware has targeted a total of 46 organizations and is now accelerating its activities with most of these in the US & Canada. Akira exfiltrates and encrypts data using a double-extortion technique with the hopes of obtaining a higher payment from the victims. Their website on the dark web provides their most recent leaks, news, contact, and other options.
Technical Details
The ransomware uses the “Microsoft Enhanced RSA and AES Cryptographic Provider” libraries with a fixed hardcoded base64 encoded public key to encrypt the victim’s machine. The malware employs several functions from CryptoAPI, including CryptAcquireContextW(), CryptImportPublicKeyInfo(), CryptGenRandom(), and CryptEncrypt().
- It first uses its API function GetLogicalDriveStrings() to get a list of the logical drives.
- It then deploys a note in the different directories and folders “akira_readme.txt”
- It then encrypts the files and directories by iterating via its API functions FindFirstFileW() and FindNextFileW()
- Encryption does exclude .exe, .dll, .sys, .msi, .lnk, .akira, and several important system file folders.
- Files are encrypted with a .akira extension, and system restore points are disabled.
Akira Expands to Linux Systems
Initially, Akira was focused on Windows Systems, but it has also now expanded to Linux platforms. Linux systems have had a low probability of being targetted with these malicious software in the past, but the growing trend among these ransomware groups are shifting their focus to Linux environments. A few groups that have targetted Linux systems include LockBit, Hive, REvil, Black basta, Black Matter, HelloKitty, Ransom EXX and AvosLocker.
Akira Linux Technical Details
- The 64 Bit executable and linkable format has a SHA256 of 1d3b5c650533d13c81e325972a912e3ff8776e36e18bca966dae50735f8ab296.
- It takes note of the encryption path, and a percentage of the files to be encrypted.
- Once executed it takes a pre-determined RSA public key to encrypt files in the system.
- Once the public key is initialized it loads a list of predetermined file extensions it tends to encrypt.
- Encrypts files with .akira and deposits its ransom note on the system.
Newer and more malicious ransomware is bound to appear as we progress into a more technologically dependent economy. The threats will always remain atop. To what end will the Akira ransomware end is yet to be seen. Nevertheless, it is important to maintain regular backups, if possible in separate networks or offline. Use basic endpoint protection software, don’t open untrusted links and attachments, and always keep your software up to date.