According to Malwarebytes Malvertising is the term for “criminally controlled advertisements” that use malicious software to intentionally harm systems in different manners. These types of advertisements typically look legitimate but they are used to deliver malicious software to end users.
In today’s Trend Micro report the BlackCat ransomware group which is also known as ALPHV has been luring end users via this method to distribute malware to end users. Not only that, but this malvertising is using a very well-known software application – WinSCP (Windows Secure Copy). WinSCP is a popular open-source Windows application that is used for file transfers. On SourceForge alone, they have over 400,000 weekly downloads which shows its popularity. Trend Micro researchers discovered that upon victims searching for WinSCP Downloads on Bing or Google, their search results pointed them to a malicious website that ranked above the typical safe organic results.
Once users visited the site above, they were directed to cloned websites of WinSCP where users downloaded both a .exe and msi.dll file. Once the executable file was launched it triggered the malware executable that ultimately contained a trojanized python310.dll. This in turn fetches information on the operating system, the hostname of the computer, checked security permissions, and access rights of objects, as well for privilege escalation and identification of files, directories, and services with weak settings. Through this infection, BlackCat is able to run additional tools, and scripts that can further compromise the system.
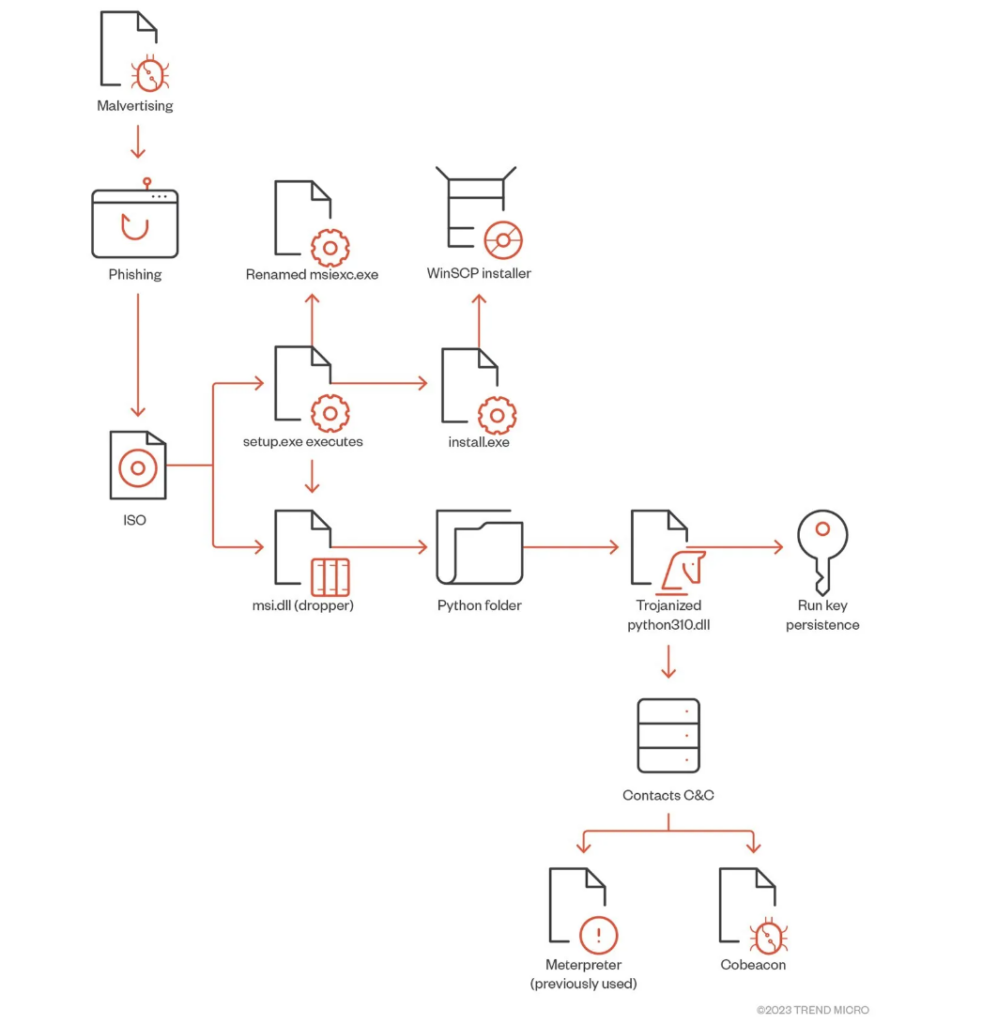
Just in this particular discovery, TrendMicro noted the following:
- Administrator privileges were obtained and then used to conduct unauthorized activities.
- Established attempts to backdoors and easy access through remote tools like AnyDesk.
- Attempts on passwords, and access to backup servers.
This malvertising showcases one of the many exploits that attackers are using on a day-to-day basis to exploit systems. We must become very aware of the websites we visit, and the software that is downloaded and then executed. Early detection is important to mitigate the damages of such vulnerability exploits.

