Yesterday, we gave a brief overview of one of the ongoing ransomware threats (Akira) and how it has expanded to the Linux system platforms. However, not moments later during the day Avast released positive news in tackling this threat. Avast mentions that their researchers have developed a decryptor for the Akira Ransomware and they have released it to the public. This is really great news for the community and victims of this specific ransomware as it will assist in recovering their data without having to pay money to cybercriminals. As Avast mentions, it is important to note that this decryptor does not work and is not related to the Akira Ransomware discovered in 2017.
Technical Details
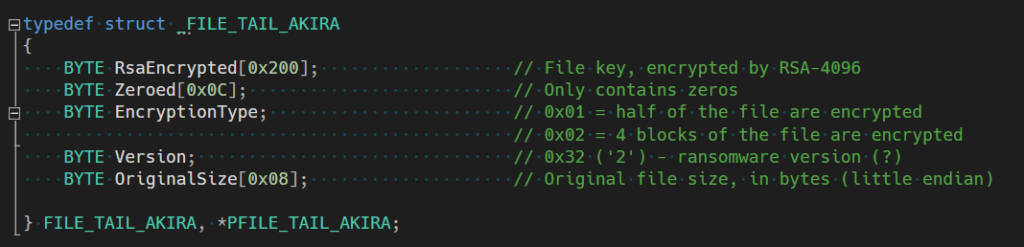
- Avast confirms that the ransomware uses a symmetric key generated by CryptGenRandom bundled with an RSA-4096 public key appended to the end of the file.
- The Linux version uses the Crypto++ library instead of the Windows CryptoAPI
- On Windows, it only encrypts a part of the file to speed things up.
- Files smaller than 2,000,000 bytes will only have half of their contents encrypted.
- While files bigger than 2,000,000 bytes will encrypt four blocks based on calculations determined by their total size.
- The Linux version allows them to determine an exact percentage of how many files should be encrypted.
Decryptor Download
Avast offers both 32 Bit and 64 Bit decryptor downloads. The 64 Bit is recommended since decryption uses a lot of system resources. Once you have downloaded the version of your preference you can run the application as Administrator, by default the application lists possible local drives.
How To Decrypt
The tricky part with this decryptor is that you need to supply both an encrypted file, and one in its original form. Avast mentions that it is important to find a file that is as big as you can find, though the encrypted file may be larger due to the encryption.
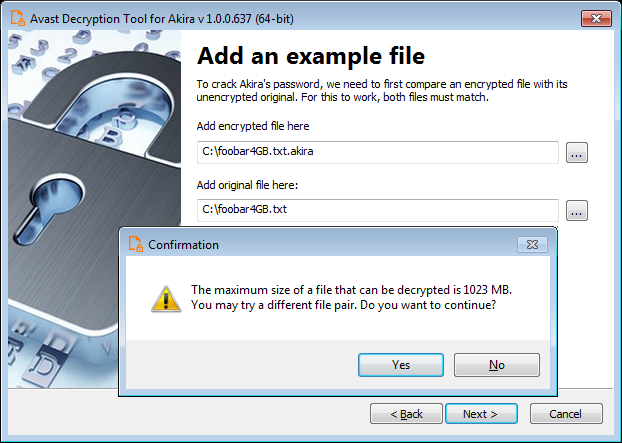
Once the password is found, then you can begin decrypting all of your files. While there is not a Linux version of the decryptor you can easily move your files to a Windows platform to perform the decryption. More detailed information can be found on Avast’s official page – https://decoded.avast.io/threatresearch/decrypted-akira-ransomware/
While there is now a decryptor, one can only expect that the persons behind Akira are most likely to revisit their code to make it an even trickier piece of malware.

